PWI000111
this document applies to :
Gripe no 0000
PowerINSPECT 4.0 can now have security settings. This enables certain users to have the ability to edit probe paths and make changes to the measurements and results of elements. This system utilises the Windows security procedures.
You have just installed PowerINSPECT and want to use the security features. First of all, you must start PowerINSPECT.
PowerINSPECT looks for the configuration files that control the security features. If these are not present they are created automatically, and basic security settings are put in place:
If you want to use the security features you need to edit the file network.opt in Notepad and change the setting called Enabled from 0 to 1. See section 3 for other details of the configuration files.
You can now edit the security settings as described above and everything should work.
There are some other things you need to do if you want to share the security settings with other computers:
The security configuration is not stored in the registry because it needs to be preserved between versions of PowerINSPECT. There are two text files using the INI file format: one local; one on the network somewhere (or it could be local in a single PC scenario).
The local configuration file is <APPDATA>\Delcam\PowerINSPECT\security.opt. <APPDATA> is the system defined location for shared application data. This is usually C:\Documents and Settings\All Users\Application Data.
The text file looks like this:
SECURITY.OPT
[Security]
NetworkPath=\\ns1\""PowerINSPECT""\tmp\network.opt
Descriptor=O:S-1-5-21-2133283647-993988769-952792173-3331G:DUD:(D;;CCDC;;;S-1-5-21-2133283647-993988769-952792173-3331)(D;;CCDC;;;SY)(A;;CCDC;;;S-1-5-21-3973020173-2796713857-643571872-1017)(A;;CC;;;S-1-5-21-2133283647-993988769-952792173-2919)
Enabled=1
LoginAtStart=1
NetworkPath: This tells PI where to find the ‘live’ security information. Typically this will be a network path. This is the only setting which is actually necessary.
Descriptor: This is a copy of the descriptor from the global configuration file. See below. This is used if the global file cannot be opened for some reason.
Enabled: This is a copy of the enabled flag from the global configuration file. See below. This is used if the global file cannot be opened for some reason.
LoginAtStart: This is a copy of the login flag from the global configuration file. See below. This is used if the global file cannot be opened for some reason.
The text file looks like this:
NETWORK.OPT
[Security]
Descriptor=O:S-1-5-21-2133283647-993988769-952792173-3331G:DUD:(D;;CCDC;;;S-1-5-21-2133283647-993988769-952792173-3331)(D;;CCDC;;;SY)(A;;CCDC;;;S-1-5-21-3973020173-2796713857-643571872-1017)(A;;CC;;;S-1-5-21-2133283647-993988769-952792173-2919)
Enabled=1
LoginAtStart=1
Descriptor: This is the text version of the security descriptor. The descriptor contains information about the access rights of each user. The access rights are set up using the GUI, and no user should ever have to look at this text directly (however, it is not encrypted, even though it looks like it might be).
Enabled: This flag determines whether the security feature of PI is being used. If not, all users have complete access to all the licenced PI features. Security access is ENABLED by default.
LoginAtStart: This flag determines whether the user is required to login when PI is starting. If not, the currently logged in user (i.e. via Windows) is used as the PI user. It is expected that most people will use the system this way, so logging in at startup is OFF by default.
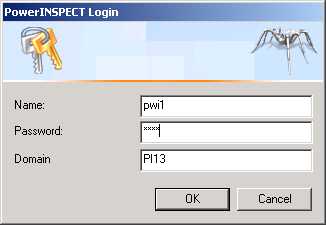
When you start PowerINSPECT , you will see the following dialog.

If you press Cancel, PowerINSPECT will exit immediately. You have to enter the same details you
use when logging onto Windows itself.
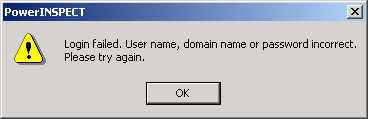
If you enter incorrect
login details, you get the following error message. There is no limit to
the number of times you can enter incorrect details.
Logging in during start up is an optional feature and is disabled by default. See the configuration files below for details.
While PowerINSPECT is running go to the menu item Tools | Login As Another User. The UI is exactly as above, except that pressing Cancel simply returns to PI without changing the user.
This is shown for Windows XP only. Windows 2000 uses a similar principle, but the details and screens will be different.
Go to Control Panel- User Accounts
Use Advanced- Advanced
Create a New User
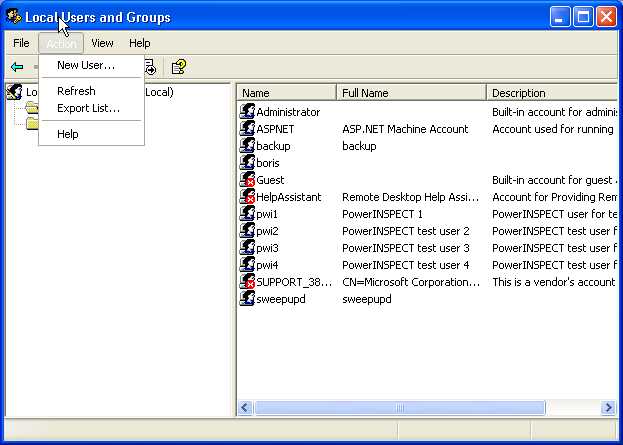
If you are logged in as an administrator, go to the menu item Tools | Manage Users and Permissions. The following screen is displayed. This is a Windows dialog, and should be familiar to Windows administrators.
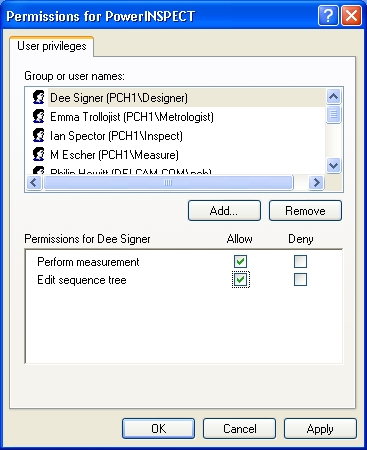
If a user does not appear in the list, they do not have any access rights. However, if a user group appears in the list, then all members of the group have the access rights granted to the group. As well as not allowing an access right, you can also explicitly deny access. Denial takes precedence over allowing access, which means you can give access to a group, but still deny it to a particular member of the group. Press Add to look for other user names to add to the list
Note: if the list of users/groups is empty, then all users and groups have access to all permissions by default. This is a feature of the Windows security system but should not be an issue for customers who actually intend to use the PI security.
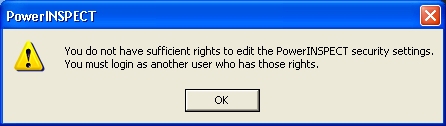
If you are not an administrator, you get the following error message.
Access rights
PI currently defines two access rights/permissions:
Perform measurement: The user can only run programs created by other users.
Edit sequence tree: The user can amend programs created by other users.
You can set up each user to have either, or neither, or both of these access rights. Having both for all users is the same as not using the security feature at all.
All users have to ability to create new PWI files. When you create a file, information is stored inside it to identify you as its owner. If you are the owner of a file, the security system is bypassed and you have full access to all licensed PI features – you can do anything to the file you like.
These two files should ideally be protected from ordinary users by the regular Windows NT file security features.
The global file only needs to be read only for most users. Administrators need write access to the file because they have the ability to modify the security descriptor and save it.
The local file is in principle written to by every user (they cache copies of the security information from the global file). However, this could create a security hole. If the file is made read only and secured from local users, the attempted writes will silently fail, but will not stop PowerINSPECT working correctly. All the file needs to contain is the path to the global file.